GHSA-26w3-q4j8-4xjp
GitHub Security Advisory
1Panel open source panel project has an unauthorized vulnerability.
Advisory Details
### Impact
The steps are as follows:
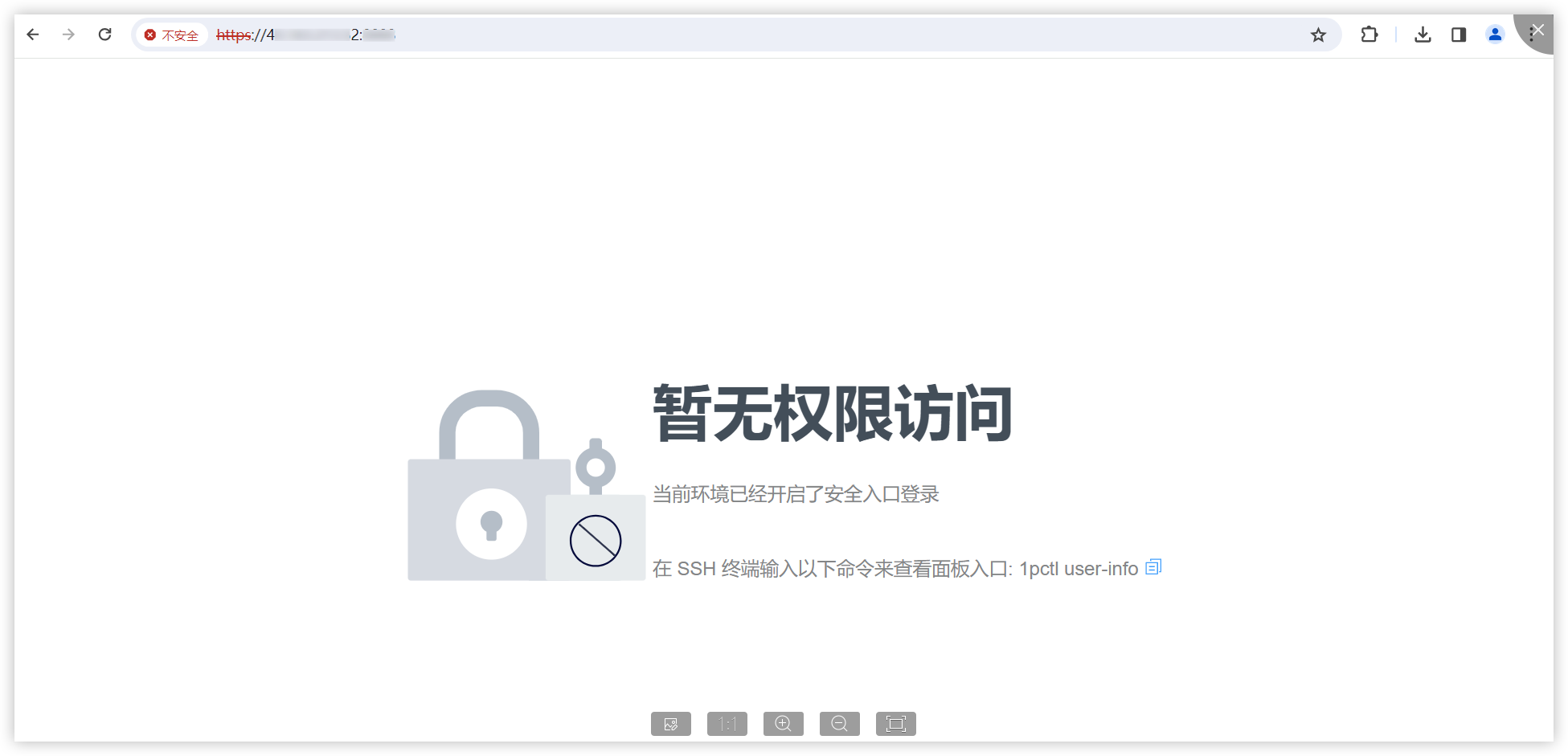
1. Access https://IP:PORT/ in the browser, which prompts the user to access with a secure entry point.
2. Use Burp to intercept:
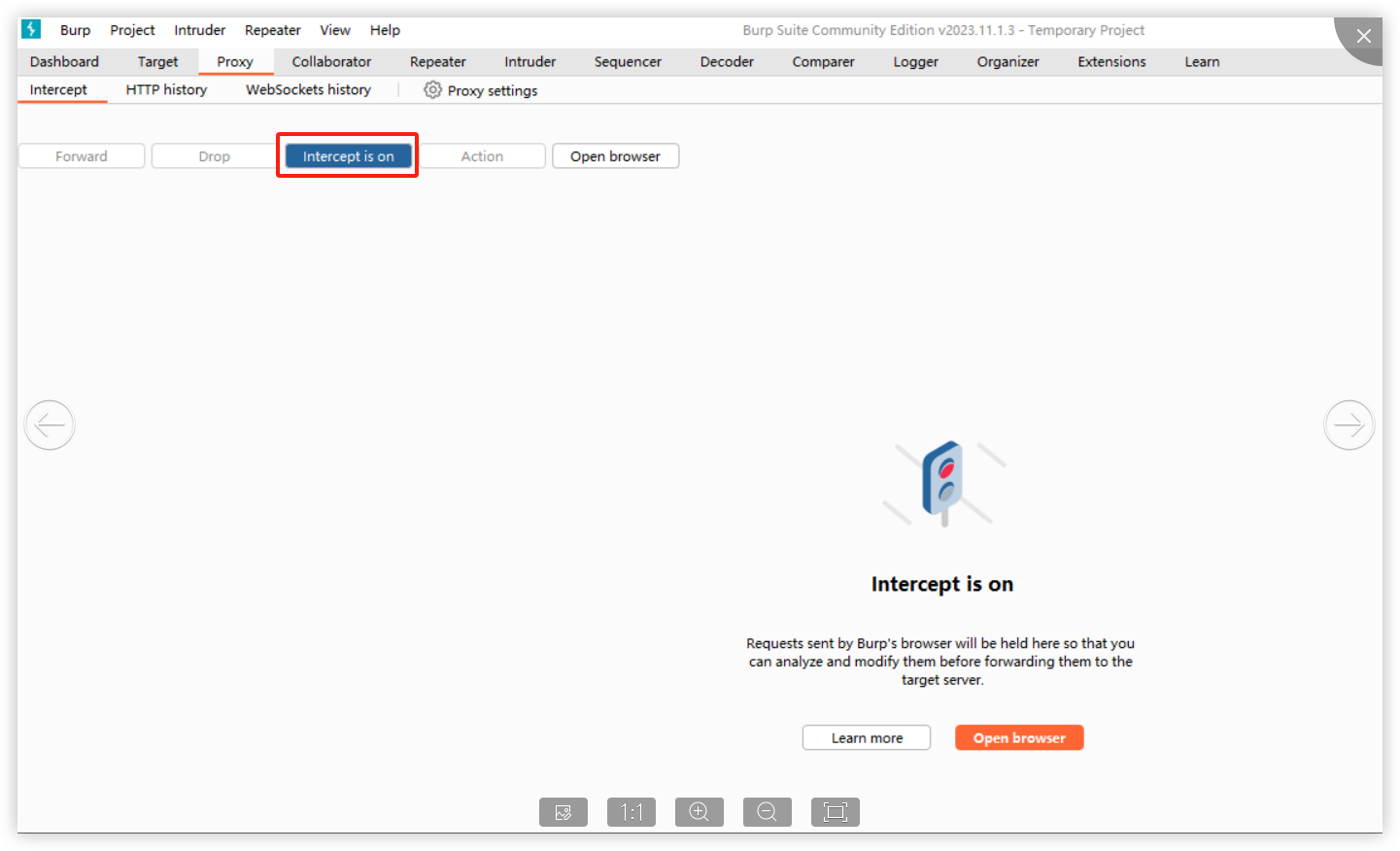
When opening the browser and entering the URL (allowing the first intercepted packet through Burp), the following is displayed:
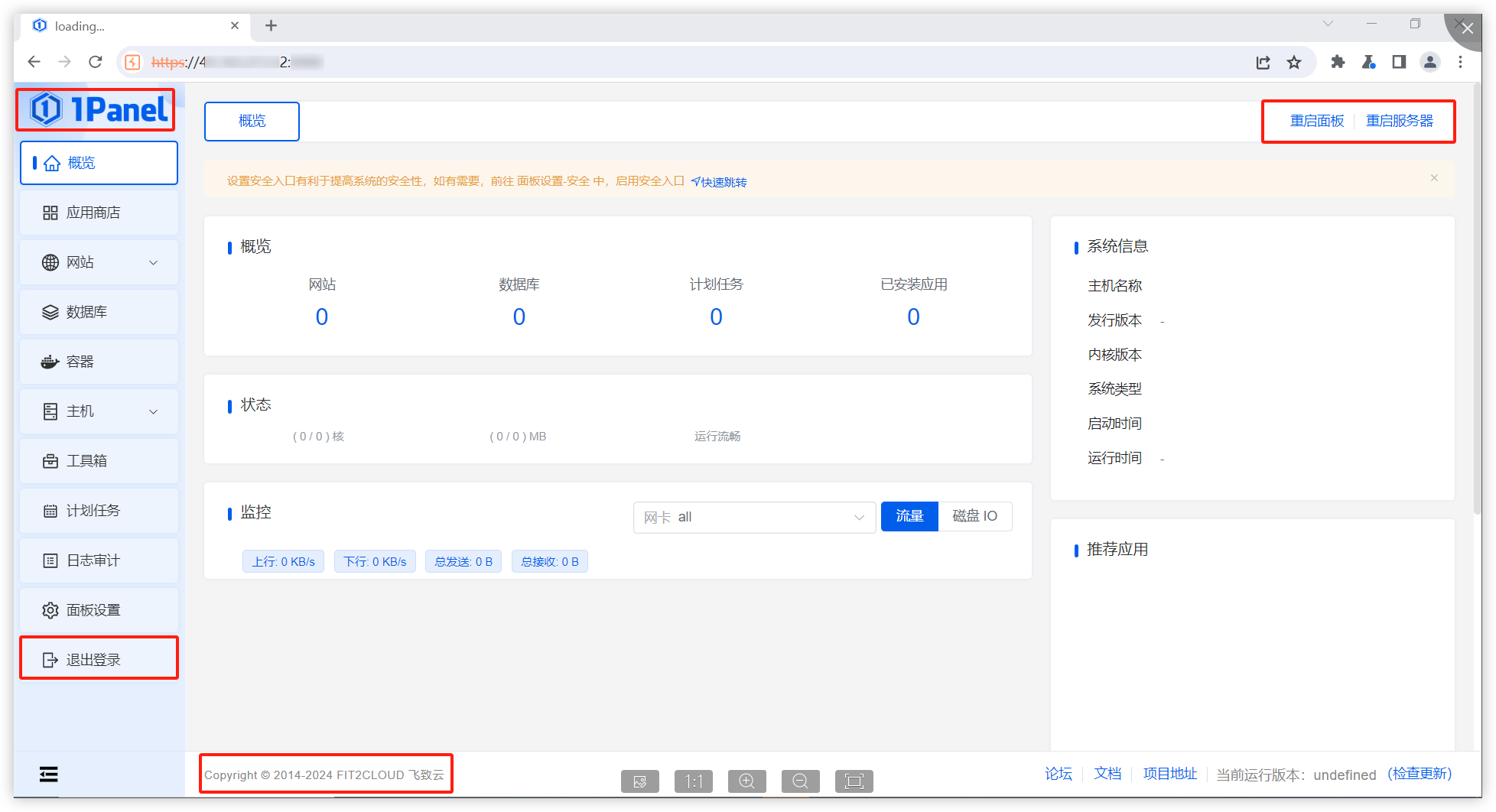
It is found that in this situation, we can access the console page (although no data is returned and no modification operations can be performed)."
Affected versions: <= 1.10.0-lts
### Patches
The vulnerability has been fixed in v1.10.1-lts.
### Workarounds
It is recommended to upgrade the version to 1.10.1-lts.
### References
If you have any questions or comments about this advisory:
Open an issue in https://github.com/1Panel-dev/1Panel
Email us at [email protected]
Affected Packages
Related CVEs
Key Information
Dataset
Data from GitHub Advisory Database. This information is provided for research and educational purposes.