GHSA-mmh6-5cpf-2c72
GitHub Security Advisory
phpMyFAQ Path Traversal in Attachments
Advisory Details
### Summary
There is a Path Traversal vulnerability in Attachments that allows attackers with admin rights to upload malicious files to other locations of the web root.
### PoC
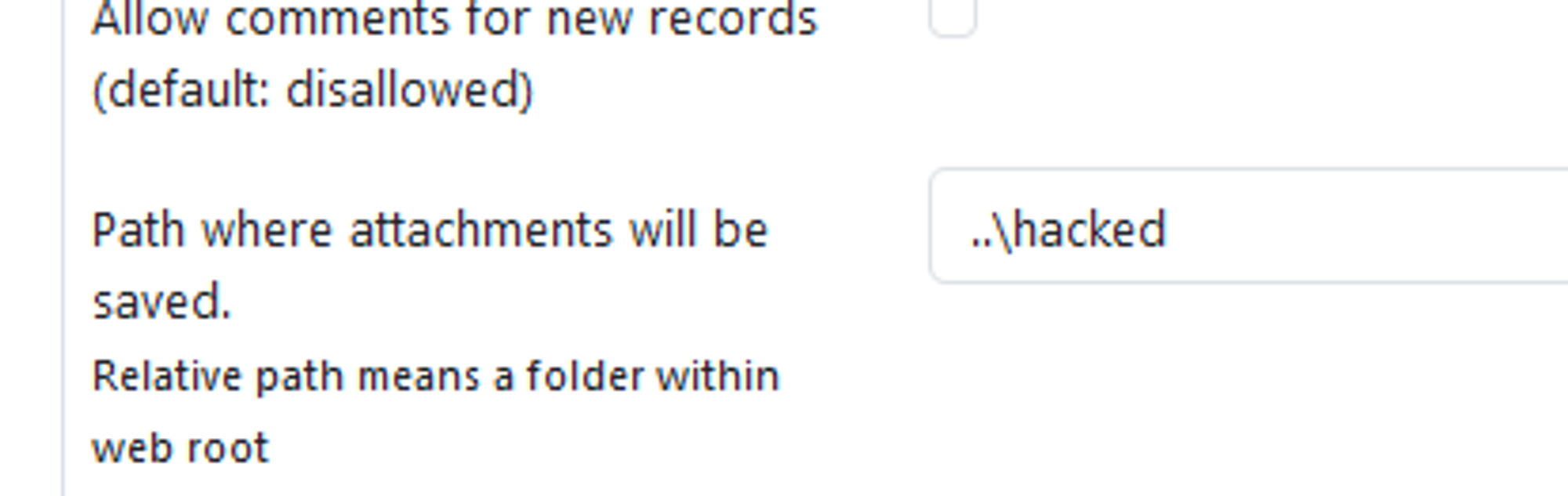
1. In settings, the attachment location is vulnerable to path traversal and can be set to e.g ..\hacked
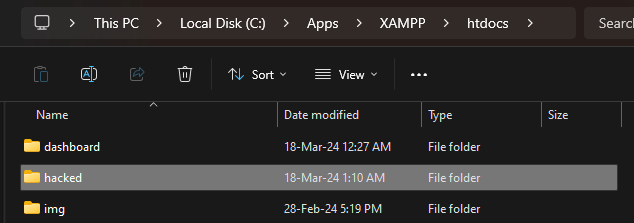
2. When the above is set, attachments files are now uploaded to e.g C:\Apps\XAMPP\htdocs\hacked instead of C:\Apps\XAMPP\htdocs\phpmyfaq\attachments
3. Verify this by uploading an attachment and see that the "hacked" directory is now created in the web root folder with the attachment file inside.
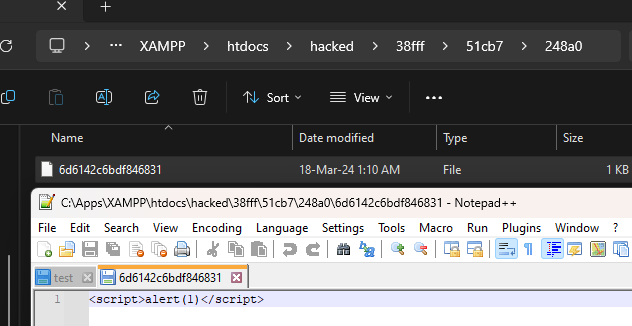
### Impact
Attackers can potentially upload malicious files outside the specified directory.
Affected Packages
Related CVEs
Key Information
Dataset
Data from GitHub Advisory Database. This information is provided for research and educational purposes.